- Encryption:
- Encryption = the process of encoding messages (usually text) in such a way that eavesdroppers or hackers cannot read it, but that authorized parties can
- Process of encryption:
- The input text
(or plaintext)
is processed by an
encryption algorithm:
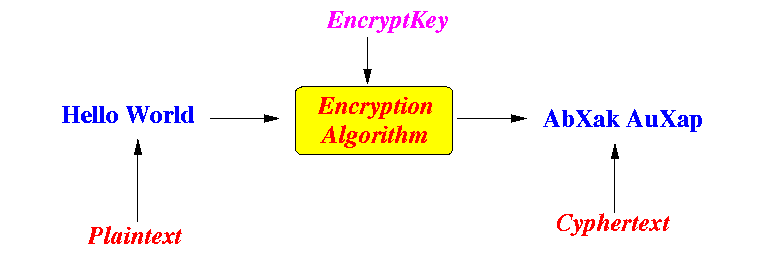
The encryption algorithm uses an additional input that changes its behavior.
- This input is called the encryption key.
The encrypted text is called cyphertext
- The cyphertext can
only be
correctly decrypted by the
decryption algorithm
using the
correct decryption key:
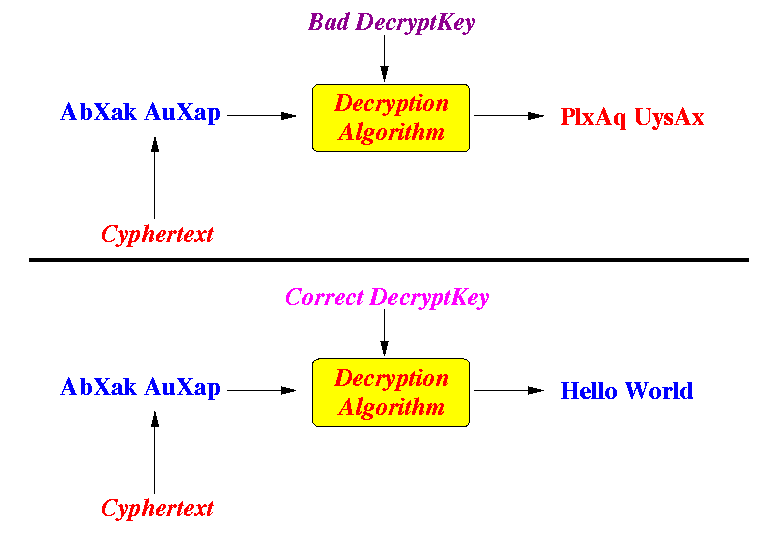
- The input text
(or plaintext)
is processed by an
encryption algorithm:
- Note:
- The encryption and
the decription algorithms
are assumed to be
public
(Meaning: everyone know exactly how the encryption and the decription algorithms operates)
- The decription key
must be kept
secret
(or else, everyone can decrypt the cyphertext !!!)
- The encryption and
the decription algorithms
are assumed to be
public
- There are two types
of encryption schemes:
- Symmetric-key schemes.
- Asymmetric-key schemes or better known as: public-key encryption.
- Symmetric-key schemes.
- Symmetric-key schemes:
- In a symmetric-key
scheme, the
encryption and
decryption keys
are the same:
encryption key == decription key
Note:
- Because the
decryption key
must be kept
secret, and
the encryption key is
equal to the
decryption key...
Therefore:
- In Symmetric-key schemes, we must keep the encryption key secret !!!
- In a symmetric-key
scheme, the
encryption and
decryption keys
are the same:
- Asymmetric-key schemes:
- In a Asymmetric-key
scheme, the
encryption and
decryption keys
are the different:
encryption key ≠ decription key
Note:
- Because the
decryption key
must be kept
secret, and
since
the encryption key is
not equal to the
decryption key...
Therefore:
- In Asymmetric-key schemes, we can publish (make public) the encryption key !!!
- In a Asymmetric-key
scheme, the
encryption and
decryption keys
are the different:
- Rot13:
- ROT13
("rotate by 13 places") is a
simple letter substitution cipher
that:
- replaces a letter x with the letter that is 13 letters after it in the alphabet.
Example:
Try it out yourself: click here
- ROT13
("rotate by 13 places") is a
simple letter substitution cipher
that:
- Note:
- There is no encryption key used in
Rot13....
- Once you find out that the cyphertext is encrypted with the Rot13 methods, you can crack it right away....
- There is no encryption key used in
Rot13....
- Caesar Cypher:
- each letter in the plaintext is replaced by a letter at some fixed number of positions down the alphabet.
Example:
- Suppose we use shift right 3 positions
to encode:
- Encode:
ABCDEFHIJKLMNOPQRSTUVWXYZ XYZABCDEFHIJKLMNOPQRSTUVW --> shift right 3 positions Plaintext: HELLO Cyphertext: DBIIL
- Decode: shift
left 3 positions
ABCDEFHIJKLMNOPQRSTUVWXYZ DEFHIJKLMNOPQRSTUVWXYZABC <-- shift left 3 positions Cyphertext: DBIIL Plaintext: HELLO
- Note:
- The encryption key used in
Caesar cypher
is the amount of shift
(direction can be encoded as positive or
negative)
- If you find out
that the cyphertext is
encrypted with
the Caesar cypher method,
you
cannot it !!
unless you know:
- the amount of shift
used in the
encoding !!!
(direction can be encoded as positive or negative)
- the amount of shift
used in the
encoding !!!
- The encryption key used in
Caesar cypher
is the amount of shift
(direction can be encoded as positive or
negative)
- Note:
- Julius Caeasar
used this encryption scheme to
send messages to his
troops
That's why this scheme is called Caesar cypher
- Julius Caeasar
used this encryption scheme to
send messages to his
troops
- Secure communication:
- Unsecure communication:
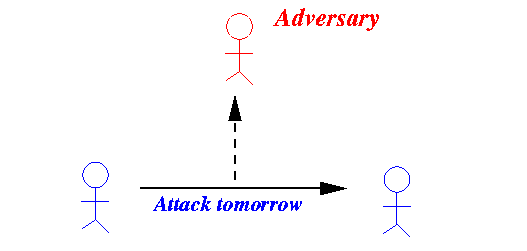
Transmissions can be intercepted
The plaintext is unsecure
- Secure communication:
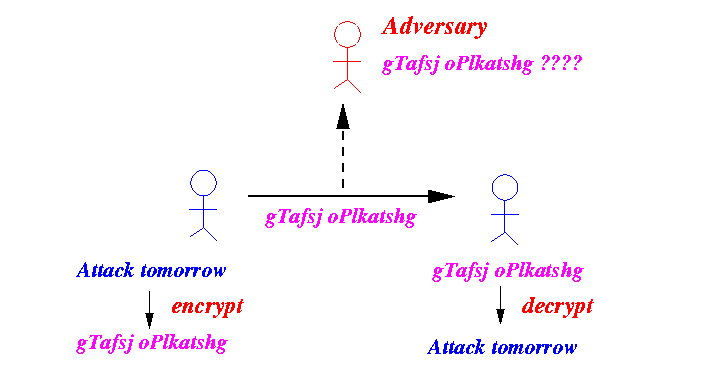
- Unsecure communication:
- Secure communication
using
symmetric key
must following the following procedure:
- Before any
secure communication
can occur,
the communicating parties
must first
obtain
the encryption/decription key:
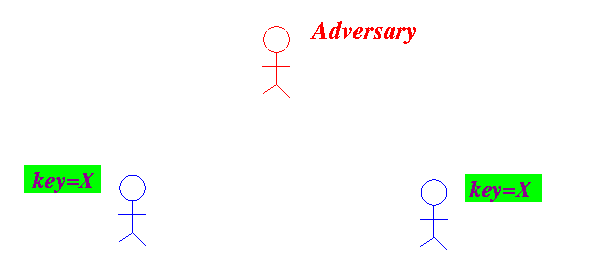
-
Secure communication
is achieved by
keeping the
key
secret:
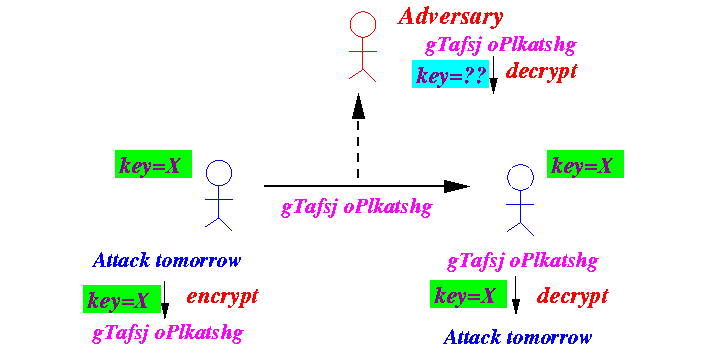
The adversary cannot decode the cyphertext because he/she does not have the key.
- Before any
secure communication
can occur,
the communicating parties
must first
obtain
the encryption/decription key:
- Where are
symmetic-key schemes
used:
- Military
- Coorporation
- Etc.
- In general:
- Symmetric-key schemes can be used
in situations where:
- the communicating parties can meet each other (in private) to establish the encryption/description key a-priori.
- Symmetric-key schemes can be used
in situations where:
- Advantage:
- Very strong security
- Messages encrypted using a symmetric-key encoding is virtually impossible to crack
- Very strong security
- Disadvantage:
- The communicating parties
must
meet in private
(at least once) to
establish a common key
before the
symmetric-key scheme
canbe used
- Consequently:
- Symmetric-key encryption is not usable to encrypt message (e.g., emails) that you want to send to someone that you have never met before...
- The communicating parties
must
meet in private
(at least once) to
establish a common key
before the
symmetric-key scheme
canbe used
- Secure communication
using
asymmetric key
must following the following procedure:
- Before any
secure communication
can occur,
each communicating party
must first
publish
his/her
encryption key:
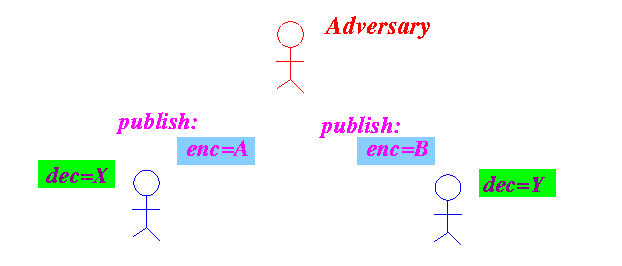
Each communicating party must keep his/her decription key secret !!!
-
Secure communication
is achieved as follows:
- The sender uses
the receipient's encoding key
to encode the message:
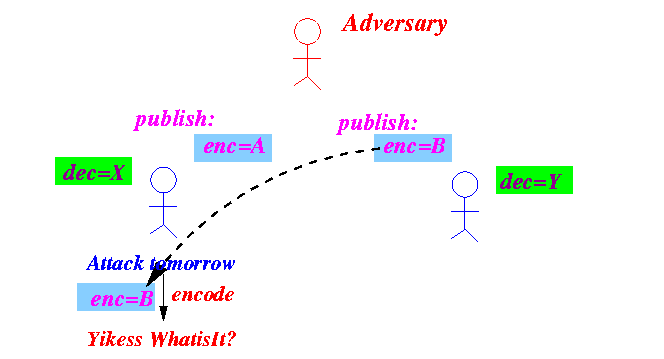
- The cyphertext sent (and may be
intercepted by the
adversary)
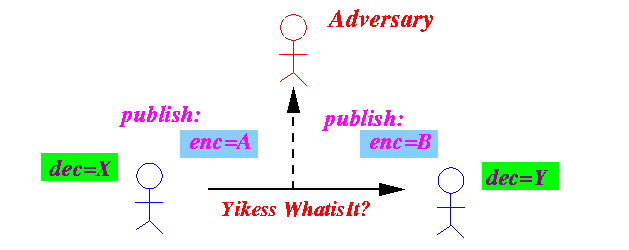
- The cyphertext can
only be decoded using
the
associated decription key:
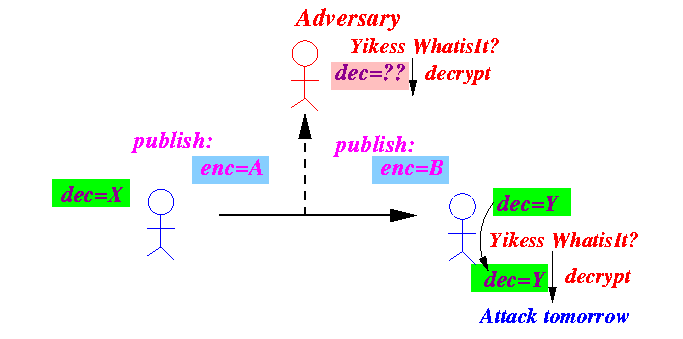
In assymetric key encoding, the cyphertext that is encoded with a encryption key can only be decode using the associated decryption key !!!
The decryption key must be kept secret !!!
- The sender uses
the receipient's encoding key
to encode the message:
- Before any
secure communication
can occur,
each communicating party
must first
publish
his/her
encryption key:
- Usages of
asymmmetric key encryption:
- Protect emails that you want to
send to someone that
you have never met before
(This kind of communication is popular in underground organizations whose members don't have the opportunity to meet in person)
- Protect emails that you want to
send to someone that
you have never met before
- Fact:
- The asymmetric key encoding
scheme cannot use
the same key
for encryption and decryption
Because:
- The encryption key must
be made public...
- If the same key is used for decryption, the adversary can crack the cyphertext easily....
- The encryption key must
be made public...
- The asymmetric key encoding
scheme cannot use
the same key
for encryption and decryption
- Historical development:
- The idea of
assymmetric key encoding was published
back in 1874 !!!
- In 1997, it was publicly disclosed that asymmetric key algorithms
were secretly developed
by James H. Ellis, Clifford Cocks, and
Malcolm Williamson at the Government Communications Headquarters (GCHQ)
in the UK in
1973.
- An asymmetric-key cryptosystem was published in 1976
by Whitfield Diffie and Martin Hellman who, influenced by
Ralph Merkle's work on public-key distribution, disclosed a method
of public-key agreement.
This method of key exchange, which uses exponentiation in a finite field, came to be known as DiffieHellman key exchange.
- This was the first published practical method for establishing a shared secret-key over an authenticated (but not private) communications channel without using a prior shared secret.
Merkle's "public-key-agreement technique" became known as Merkle's Puzzles, and was invented in 1974 and published in 1978.
- This was the first published practical method for establishing a shared secret-key over an authenticated (but not private) communications channel without using a prior shared secret.
- A generalization
of Cocks's scheme was independently invented in
1977
by
Ron Rivest, Adi Shamir and Leonard Adleman,
all then at MIT.
- Their scheme is commonly known as:
RSA encryption
---
Wikipedia page
- The RSA method is now the most popular public key encryption method.
- Their scheme is commonly known as:
RSA encryption
---
Wikipedia page
- The idea of
assymmetric key encoding was published
back in 1874 !!!